Decoding Internet Explorer Cookies
Posted by Robert Rutherford on February 26th, 2011 under Cookie, Cookies, Decoding, Forensic Analysis, Internet Explorer, MicrosoftViewing and decoding Internet Explorer Cookie data within NetAnalysis is a simple task. First of all, make sure you have the cookie files and corresponding INDEX.DAT file extracted from your forensic image.
Import the INDEX.DAT file into NetAnalysis. To activate the Cookie decoder by selecting Cookie Decoder from the View menu or by selecting the Cookie Decoder button on the main toolbar.
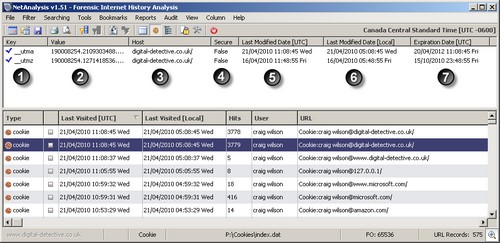
When you select a cookie entry from the index entries, if a corresponding cookie file is available in the cookie folder, NetAnalysis will open it and decode the cookie entries, as shown in Figure 1.
Figure 1
Cookies hold data in Name/Value pairs. In the example above, this Cookie contains two records. Each record contains a Name/Value pair.
Column 1 has a blue tick next to it. This is for indication only and shows whether the cookie is expired when compared to today’s date and time. This is just an indicator and has no evidential meaning. Column 1 also contains the Name or Key portion of the Name/Value pair.
Column 2 contains the value portion. It is not unusual to see some web sites storing multiple Name/Value pairs in one value field. This obviously cuts down on the number of cookies that need to be set and retrieved.
Column 3 shows the Host portion of the record.
Column 4 shows the security of the transportation method. Even if the Cookie is secure, it is stored in plain text on the system.
Column 5 shows the Last Modified Date/Time in UTC. Internet Explorer Cookie times are stored as a UTC 64 bit FILETIME structure within the text file.
Column 6 shows the Column 5 Date/Time converted to Local Time. NetAnalysis converts the time stamp from UTC to Local time based on the Time Zone set by the Investigator prior to importing the INDEX.DAT data.
Column 7 shows the Expiration date of the Cookie in UTC.
Published by Robert Rutherford
Recent Posts
Recent Comments
- Mark McGinty on Internet Explorer INTERNET_CACHE_ENTRY_INFO Structure
- ZubenElSchemali on Digital Evidence Discrepancies – Casey Anthony Trial
- admin on NetAnalysis Training Announcement
- Brad Berghuis on NetAnalysis Training Announcement
- J Townsend on Digital Evidence Discrepancies – Casey Anthony Trial
Archives
- May 2021
- May 2014
- April 2014
- February 2014
- January 2014
- October 2012
- June 2012
- May 2012
- April 2012
- March 2012
- February 2012
- January 2012
- December 2011
- November 2011
- October 2011
- September 2011
- July 2011
- March 2011
- February 2011
- January 2011
- November 2010
- October 2010
- September 2010
- August 2010
- July 2010
- June 2010
- May 2010
- April 2010
- March 2010
Categories
- Apple Safari (2)
- Evidence (3)
- Forensic Analysis (17)
- Forensic Software (14)
- Google Chrome (5)
- Internet Explorer (14)
- Legal (3)
- Mozilla Firefox (10)
- News (14)
- Opera (4)
- Security (7)
- Training (2)
Sidebar
This is your sidebar, you can add content here in the widgets section of admin panel