Random Cookie Filenames
Posted by Robert Rutherford on September 14th, 2011 under Cookie, Cookies, Forensic Analysis, IE10, IE11, IE9, Internet Explorer, Microsoft, Windows 7, Windows 8As forensic examiners will be aware, Microsoft Internet Explorer stores cached data within randomly assigned folders. This behaviour was designed to prevent Internet data being stored in predictable locations on the local system in order to foil a number of attack types. Prior to the release of Internet Explorer v9.0.2, cookies were an exception to this behaviour and their location was insufficiently random in many cases.
Cookie Files
Generally, for Vista and Windows 7, cookie files are stored in the location shown below:
|
Microsoft Windows Internet Explorer Cookie Location |
|
AppDataRoamingMicrosoftWindowsCookies |
Table 1
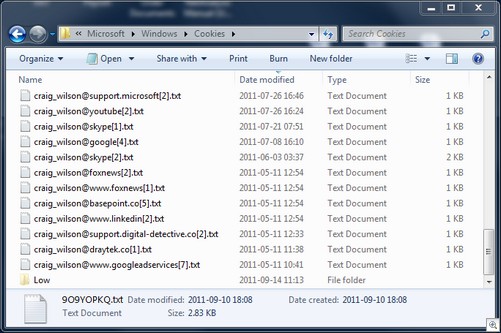
The cookie filename format was the user’s login name, the @ symbol and then a partial hostname for the domain of the cookie.
Figure 1
With sufficient information about a user’s environment, an attacker might have been able to establish the location of any given cookie and use this information in an attack.
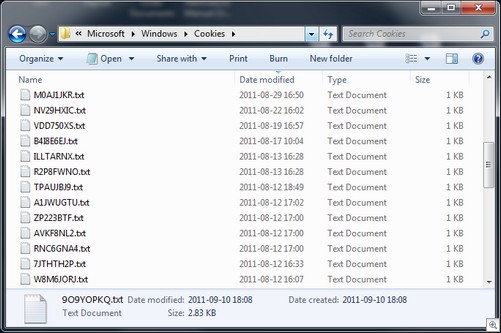
To mitigate the threat, Internet Explorer 9.0.2 now names the cookie files using a randomly-generated alphanumeric string.Older cookies are not renamed during the upgrade, but are instead renamed as soon as any update to the cookie data occurs.Figure 2 shows an updated cookie folder containing the new files.
Figure 2
This change will have no impact on dealing with the examination of cookie data.It will obviously no longer be possible to identify which domain a cookie belongs to from just the file name.
Published by Robert Rutherford
Recent Posts
Recent Comments
- Mark McGinty on Internet Explorer INTERNET_CACHE_ENTRY_INFO Structure
- ZubenElSchemali on Digital Evidence Discrepancies – Casey Anthony Trial
- admin on NetAnalysis Training Announcement
- Brad Berghuis on NetAnalysis Training Announcement
- J Townsend on Digital Evidence Discrepancies – Casey Anthony Trial
Archives
- May 2021
- May 2014
- April 2014
- February 2014
- January 2014
- October 2012
- June 2012
- May 2012
- April 2012
- March 2012
- February 2012
- January 2012
- December 2011
- November 2011
- October 2011
- September 2011
- July 2011
- March 2011
- February 2011
- January 2011
- November 2010
- October 2010
- September 2010
- August 2010
- July 2010
- June 2010
- May 2010
- April 2010
- March 2010
Categories
- Apple Safari (2)
- Evidence (3)
- Forensic Analysis (17)
- Forensic Software (14)
- Google Chrome (5)
- Internet Explorer (14)
- Legal (3)
- Mozilla Firefox (10)
- News (14)
- Opera (4)
- Security (7)
- Training (2)
Sidebar
This is your sidebar, you can add content here in the widgets section of admin panel